- Home
- Sustainability Management
- Information Security Management
Information Security and Risk Management
Increasing customer value is one of iST’s goals so long as the Company exists. As a professional technical service provider, iST knows well that the provision of accurate and precise data can accelerate the customer’s progress in R&D. Considering that relevant analytical data is the customer’s property and brainchild, the data must be kept in good custody.
Information Security and Management Structure
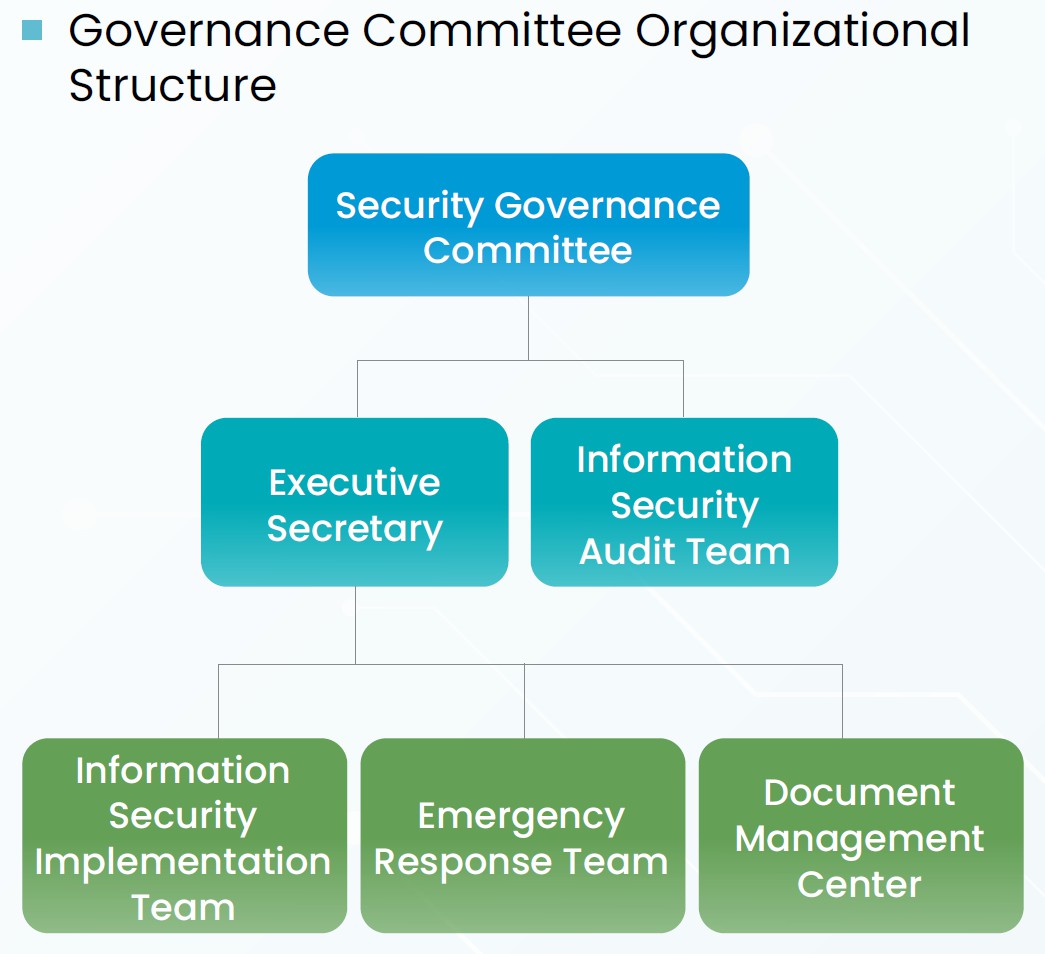
To ensure the security of iST’s and the customers’ information assets, the Company has set up a Security Governance Committee to integrate internal resources and perform information security risk assessment as well as developing annual information security plans and inspection standards. We also coordinate relevant resources and activities across units to implement various information security controls, annual education and training on information security for employees, and information security audits. The Security Governance Committee hold meetings biannually to review and resolve on information security and protection guidelines and policies in order to realize the effectiveness of the information security management measures. The committee may also hold a meeting from time to time based on the needs of management of information security risk. The convener of the Security Governance Committee represents the committee and reports to the board of directors every year. iST obtained the certification of ISO/IEC 27001 Information Security Management System (ISMS) since 2020. Every three years, it passes the audit validity review.The validity of certification expires on Oct. 15, 2026.
Information Security Management System the Chief Information Security Officer is the convener of the meeting of security control committee, with Heads of Divisions as ex officio members, Information Security Implementation Team, Emergency Response Team, Information Security Audit Team and Document Management Center. A total of 24 people as listed above.
iST establishes various information security measures through three operating policies – “Establishing a dedicated information security organization,” “Obtaining support from senior management,” “Implementing all-staff participation,” and in compliance with relevant requirements of ISO/IEC 27001 information security management system, such as information security policies, management procedures, and operating standards, in order to safeguard the security and interests of iST and its customers’ information assets.
Information security policy and specific management plan
| Information Security Policy Vision | Information Security |
| Strengthening knowledge and skills of personnel |
Hold educational training on information security to enhance employees′ awareness of information security and strengthen their awareness of relevant responsibilities.
|
| Avoiding information disclosure |
Protect information of iST′s business activities, prevent unauthorized access and modification and ensure accuracy and completeness of information.
|
| Conducting routine maintenance works |
Conduct internal and external audits periodically to ensure implementation of relevant operations.
|
| Ensuring services being available |
Ensure a certain level of availability of iST′ s key core systems.
|
iST enhances the personnel’s awareness of information security and overall security resilience through“Establishing Multifaceted Information Security Message Communication” and “Implementing Information Security Educational Training”.
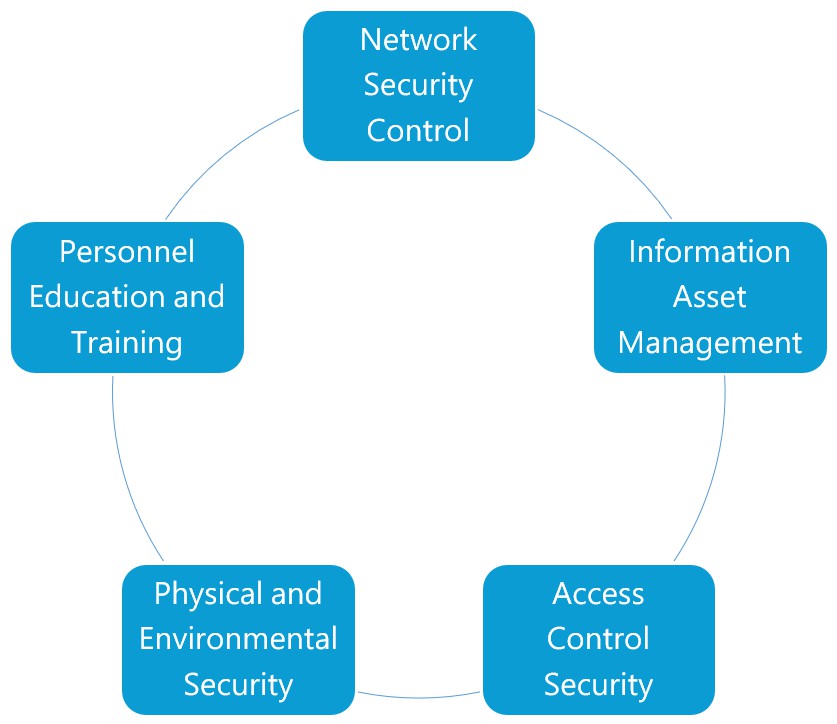
iST information security technical measures are planned and implemented in five major aspects to continuously strengthen information security protection capabilities.
Allocate resources for cybersecurity management
To achieve the vision of our cybersecurity policy, we have allocated resources to implement the following cybersecurity protection measures:
| Information security protection measures | |
| Strengthening knowledge and skills of personnel |
|
| Avoiding information disclosure |
|
| Conducting routine maintenance works |
|
| Ensuring services being available |
|
Information Security and Risk Management
Increasing customer value is one of iST’s goals so long as the Company exists. As a professional technical service provider, iST knows well that the provision of accurate and precise data can accelerate the customer’s progress in R&D. Considering that relevant analytical data is the customer’s property and brainchild, the data must be kept in good custody.
Information Security and Management Structure
To ensure the security of iST’s and the customers’ information assets, the Company has set up a Security Governance Committee to integrate internal resources and perform information security risk assessment as well as developing annual information security plans and inspection standards. We also coordinate relevant resources and activities across units to implement various information security controls, annual education and training on information security for employees, and information security audits. The Security Governance Committee hold meetings biannually to review and resolve on information security and protection guidelines and policies in order to realize the effectiveness of the information security management measures. The committee may also hold a meeting from time to time based on the needs of management of information security risk. The convener of the Security Governance Committee represents the committee and reports to the board of directors every year. iST obtained the certification of ISO/IEC 27001 Information Security Management System (ISMS) since 2020. Every three years, it passes the audit validity review.The validity of certification expires on Oct. 15, 2026.
Information Security Management System the Chief Information Security Officer is the convener of the meeting of security control committee, with Heads of Divisions as ex officio members, Information Security Implementation Team, Emergency Response Team, Information Security Audit Team and Document Management Center. A total of 24 people as listed above.
iST establishes various information security measures through three operating policies – “Establishing a dedicated information security organization,” “Obtaining support from senior management,” “Implementing all-staff participation,” and in compliance with relevant requirements of ISO/IEC 27001 information security management system, such as information security policies, management procedures, and operating standards, in order to safeguard the security and interests of iST and its customers’ information assets.

Information security policy and specific management plan
| Information Security Policy Vision | Information Security |
| Strengthening knowledge and skills of personnel |
Hold educational training on information security to enhance employees′ awareness of information security and strengthen their awareness of relevant responsibilities.
|
| Avoiding information disclosure |
Protect information of iST′s business activities, prevent unauthorized access and modification and ensure accuracy and completeness of information.
|
| Conducting routine maintenance works |
Conduct internal and external audits periodically to ensure implementation of relevant operations.
|
| Ensuring services being available |
Ensure a certain level of availability of iST′ s key core systems.
|
iST enhances the personnel’s awareness of information security and overall security resilience through“Establishing Multifaceted Information Security Message Communication” and “Implementing Information Security Educational Training”.
iST information security technical measures are planned and implemented in five major aspects to continuously strengthen information security protection capabilities.

Allocate resources for cybersecurity management
To achieve the vision of our cybersecurity policy, we have allocated resources to implement the following cybersecurity protection measures:
| Information security protection measures | |
| Strengthening knowledge and skills of personnel |
|
| Avoiding information disclosure |
|
| Conducting routine maintenance works |
|
| Ensuring services being available |
|




